Windows Basic Concepts
Here I want to describe some important questions and their answers. So please read carefully its very important facts in windows servers.
1) What is Active Directory?
Ans: An Active Directory (AD) structure is a hierarchical framework of objects which include resources (e.g. printers) , services (e.g. e-mail ), and users (accounts, or users and groups) or we can say AD is a repository service of enterprise wide data
2) What are FSMO Roles? Explain Each Role?
Ans: Although most operations, such as creating a user, are multi-mastered, and can be made by connecting to any available domain controller, some operations are still handled only by designated domain controllers. Microsoft sometimes calls this the Flexible Single Master Operation (FSMO) roles. There are five FSMO roles.
Two of these are per forest:
1) Schema Master: There is only one DC in the forest acting as the Schema Master. It holds the master copy of the Schema.
2) Domain Naming Master: There is only one DC in the forest acting as the Domain Naming Master. It authorizes the creation and deletion of domains in the forest.
Within each domain there are three further roles.
3) PDC emulator: Each domain has a PDC emulator. As its name suggests it provides compatibility with legacy (NT4) DCs and clients. It also functions as the domain master browser, source for time synchronization within the domain, and the single mastering of Group Policies.
4) RID Master: Each domain also has a RID Master. The RID Master generates a pool of Relative IDentifiers and allocates them to other DCs in its domain. Each DC can use a RID from its pool whenever it needs to generate a SID (Security IDentifier) for any new security principals object (users, groups or computers) that is created. A SID is a globally unique identifier for a security principal. The RID master is also used to single master the movement of security principals from one domain to another.
5) Infrastructure Master: Finally, each domain has an Infrastructure Master (IM). The IM periodically looks up references to external objects by consulting the global catalog. An example of an 'external object' would be if you added a user from one Domain A to a group in Domain B. As far as Domain B is concerned the user is an external object. The IM is checking to see if any details about that foreign object (such as its distinguished name or SID) have changed.
3) What is a Global Catalog?
Ans: The Global Catalog (GC) has two primary functions. First, it acts as a domain controller that stores object data and manages queries about objects and their most common attributes (called the Global Catalog Partial Attribute Set, or PAS). Second, it provides data that permits network logon. GC provides a listing of all objects in AD so we can query GC for any information needed. LDAP (light weight directory access protocol) is used (by AD) to query the GC on port 3268.
4) What are Group Policies?
Ans: Group policies are used by administrators to configure and control user environment settings. Group Policy Objects (GPOs) are used to configure group policies which are applied to sites, domains, and organizational units (OUs). Settings that do the following may be applied with group policy: Manage user environments - Wallpaper and other settings. Manage scripts - Logon/logoff and startup/shutdown scripts. Manage security - Event log settings, account policies, and more. Manage software deployment - Applications may be automatically installed when the client computer starts. Redirect folders - Folders on a local computer may be redirected to a network share.
5) What is the difference between a Domain and Workgroup?
Ans: A domain is a group of computers and devices on a network that are administered as a unit with common rules and procedures. Within the Internet, domains are defined by the IP address. All devices sharing a common part of the IP address are said to be in the same domain.
Workgroup computing occurs when all the individuals have computers connected to a network (a group of two or more computer systems linked together) that allows them to send e-mail to one another, share data files, and other resources such as printers. Normally, a workgroup is limited to 10 network devices/computers. Since workgroup machines might have different account names, you really have to know the admin account for each specific machine in order to effectively manage the workgroup.
6) What is the relationship between tree and a forest?
Ans: The framework that holds the objects is viewed at a number of levels. At the top of the structure is the Forest - the collection of every object, its attributes and rules (attribute syntax) in the AD. The forest holds one or more transitive, trust-linked Trees. A tree holds one or more Domains and domain trees, again linked in a transitive trust hierarchy. Domains are identified by their DNS name structure, the namespace. A domain has a single DNS name.
The objects held within a domain can be grouped into containers called Organizational Units (OUs). OUs give a domain a hierarchy, ease its administration, and can give a semblance of the structure of the AD's company in organizational or geographical terms. OUs can contain OUs - indeed, domains are containers in this sense - and can hold multiple nested OUs. Microsoft recommends as few domains as possible in AD and a reliance on OUs to produce structure and improve the implementation of policies and administration. The OU is the common level at which to apply group policies, which are AD objects themselves called Group Policy Objects (GPOs), although policies can also be applied to domains or sites (see below). The OU is the lowest level at which administrative powers can be delegated.
[To allow users in one domain to access resources in another, AD uses trust. Trust is automatically produced when domains are created.]
7) What is the file name of Active directory and where is it stored?
Ans: C:/Windows/NTDS/Ntds.dit
8) What is backup? What are the different types of backups explain them?
Ans: Backup Is creating a replica of data on a server/PC. Backups could be taken on another disk or magnetic tape for offsite storage. Types of backup are:
I) normal or full backup: the entire backup for the day
ii) Incremental backup: backup since last backup
iii) Differential backup: backup since last full backup
9) Where is System State and what does it contain?
10) What is the difference between NTFS and FAT file system?
Ans: FAT (file allocation table): FAT16 & 32
NTFS (new technology file system): has an additional feature such as Security & File compression (not both at same time)
You can convert a partition from FAT to NTFS but not vice versa. To do so, open an MS-DOS Prompt window and type the following command:
CONVERT drive: /FS: NTFS
For example, if you want to convert your D drive to NTFS, you'd replace the word drive with the letter D, as follows:
CONVERT D: /FS: NTFS
11) How do you install Active Directory?
Ans: in command prompt: use the command DCPromo FOR INSTALL / UNINSTALL. If it is installed the command would uninstall it or if it is not installed it will install it.
12) What is DNS?
Ans: Domain naming system is responsible for resolving names to IP address.
13) What is router frequency, NAT, how it works, what router does, which protocol it uses?
Ans: 2.4GHZ. Network address translation (NAT) separates external network or internet from internal network/intranet. Router operates on network layer.
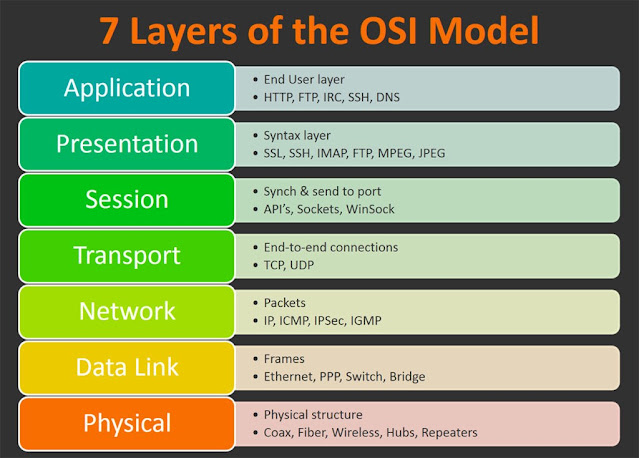
14) OSI model & protocols in each layer?
Ans: The OSI model describes a fixed, seven layer stack for networking protocols.
7. APPLICATION: HTTP, SMTP, SNMP, FTP, Telnet, ECHO, SIP, SSH, NFS, RTSP, XMPP, Whois, ENRP
6. PRESENTATION: XDR, ASN.1, SMB, AFP, NCP.
5. SESSION: ASAP, TLS, SSL, ISO 8327 / CCITT X.225, RPC, NetBIOS, ASP. Establishing & managing sessions.
4. TRANSPORT: TCP, UDP, RTP, SCTP, SPX, ATP, IL. This layer is for flow control.
3. NETWORK: IP, ICMP, IGMP, IPX, BGP, OSPF, RIP, IGRP, EIGRP, ARP, RARP, X.25. Router works on network layer. Connecting over a network.
2. DATA LINK: Ethernet, Token ring, HDLC, Frame relay, ISDN, ATM, 802.11 WiFi, FDDI, PPP. Switch works on this layer.
1. PHYSICAL: 10BASE-T, 100BASE-T, 1000BASE-T, SONET/SDH, T-carrier/E-carrier, various 802.11 physical layers. Hubs & repeaters operate on this layer.
TCP/IP model:
4 Application: DNS , TFTP , TLS/SSL, FTP, HTTP , IMAP , IRC , NNTP ,POP3 ,SIP ,SMTP,SNMP ,SSH ,TELNET ,ECHO ,Bit Torrent, RTP , PNRP , rlogin , ENRP, …
Routing protocols like BGP <Border_Gateway_Protocol> and RIP , which for a variety of reasons run over TCP and UDP respectively, may also be considered part of the application or network layer.
3 Transport: TCP ,UDP ,DCCP ,SCTP ,IL ,… Routing protocols like OSPF <Open_shortest_path_first>, which run over IP, may also be considered part of the transport or network layer. ICMP and IGMP <Internet_group_management_protocol> run over IP may be considered part of the network layer.
2 Network: IP , ARP and RARP operate underneath IP but above the link layer so they belong somewhere in between.
1 Link: Ethernet , Wi-Fi , Token ring , PPP, SLIP , FDDI <Fiber_distributed_data_interface>, ATM , Frame Relay, SMDS , …
15) What is ping?
Ans: Packet internet gropher & it uses ICMP protocol. It is used to check connectivity to an IP or PC name. try ping command on your PC & check for replies.
16) What r the boot options for a PC. List them & which option do we use & when?
Ans: When PC reboots press F8 so you reach the boot options.
a) Safe Mode: This starts Windows using only basic drivers and no network connection. Safe Mode allows a Windows PC to start using default settings (VGA display driver, Microsoft mouse, no network connection, minimal device drivers) so that you can perform a system repair. These options often allow you to repair your Windows configuration without performing a complete re-installation of the system software. For example, if you have installed an application that subsequently prevents Windows from starting, you should be able to start in Safe Mode so that you can remove the offending application.
b) Safe Mode with Networking: This is useful if you need to connect to CFS to install new drivers from the shared copy of installation files.
c) Safe Mode with Command Prompt: This startup option does not start the Windows GUI. However VGA drivers are installed so the option is very similar to basic Safe Mode.
d) Enable Boot Logging: This starts Windows whilst logging all devices and services that are loaded in a file, NTBTLOG.TXT, in the Windows directory. A log is always created by the preceding three Safe Mode options.
e) Enable VGA Mode: This option specifically addresses the problems which occur when a video driver prevents Windows from starting.
f) Last Known Good Configuration: If Windows fails to start successfully, try the option Last Known Good Configuration before all others including Safe Mode. This starts Windows using the registry information it saved at the last successful shutdown and it can correct basic configuration problems. It does not solve problems caused by incorrect or missing files.
g) Directory Services Restore Mode: For Windows 2000 and 2003 servers only.
h) Debugging Mode: Diagnostic tool for experienced managers.
i) Disable automatic restart on system failure: Windows XP only: If Windows experiences a critical error on startup; a blue screen error (BSOD) message may be displayed before the system restarts. This option allows you to disable the automatic restart so that the error message can be read.
17) Mother board components?
Ans: Central Processing Unit (CPU), underlying circuitry, expansion/PCI slots, video components, random access memory (RAM) slots, and a variety of other chips.
18) What is firewall, How to change settings for windows firewall, 3rd party firewalls?
Ans: A system designed to prevent unauthorized access to or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria.
If you right click on local area connection icon you will get the option to change windows firewall settings. You can also start or stop the service from services menu by typing services.msc in run window & then selecting the service.
3rd party firewalls are Norton or Symantec, McAfee, AVG, etc.
19) Proxy server?
Ans: Proxy server: Intercepts all messages entering and leaving the network. The proxy server effectively hides the true network addresses.
A server that sits between a client application, such as a Web browser, and a real server. It intercepts all requests to the real server to see if it can fulfill the requests itself. If not, it forwards the request to the real server.
20) Enabling file & printer sharing?
- Ans: Run the Network Setup wizard.
- Click the connection method that applies for your computer.
- Accept the default computer description and computer name.
- Accept the default workgroup name. This name should match the workgroup name of the other computers that you want to share files with.
21) Difference between switch & hub & router, layers on which they work?
Ans: Switch:-A network switch is networking hardware that connects devices on a computer network by using packet switching to receive and forward data to the destination device. A network switch is a multiport network bridge that uses MAC addresses to forward data at the data link layer of the OSI model.
Router:-A router is a networking device that forwards data packets between computer networks. ... A packet is typically forwarded from one router to another router through the networks that constitute an internetwork (e.g. the Internet) until it reaches its destination node.
Hub:-Hubs are devices commonly used to connect segments of a LAN.
22) Boot sequence of PC?
Ans: For System Boot Sequence go through this:
The system BIOS is what starts the computer running when you turn it on. The following are the steps that a typical boot sequence involves. Of course this will vary by the manufacturer of your hardware, BIOS, etc., and especially by what peripherals you have in the PC. Here is what generally happens when you turn on your system power:
- The internal power supply turns on and initializes. The power supply takes some time until it can generate reliable power for the rest of the computer, and having it turn on prematurely could potentially lead to damage. Therefore, the chipset will generate a reset signal to the processor (the same as if you held the reset button down for a while on your case) until it receives the Power Good signal from the power supply.
- When the reset button is released, the processor will be ready to start executing. When the processor first starts up, it is suffering from amnesia; there is nothing at all in the memory to execute. Of course processor makers know this will happen, so they pre-program the processor to always look at the same place in the system BIOS ROM for the start of the BIOS boot program. This is normally location FFFF0h, right at the end of the system memory. They put it there so that the size of the ROM can be changed without creating compatibility problems. Since there are only 16 bytes left from there to the end of conventional memory, this location just contains a "jump" instruction telling the processor where to go to find the real BIOS startup program.
- The BIOS performs the power-on self test (POST). If there are any fatal errors, the boot process stops. POST beep codes can be found in this area of the Troubleshooting Expert.
- The BIOS looks for the video card. In particular, it looks for the video card's built in BIOS program and runs it. This BIOS is normally found at location C000h in memory. The system BIOS executes the video card BIOS, which initializes the video card. Most modern cards will display information on the screen about the video card. (This is why on a modern PC you usually see something on the screen about the video card before you see the messages from the system BIOS itself).
- The BIOS then looks for other devices' ROMs to see if any of them have BIOSes. Normally, the IDE/ATA hard disk BIOS will be found at C8000h and executed. If any other devices BIOSes are found, they are executed as well.
- The BIOS displays its startup screen.
- The BIOS does more tests on the system, including the memory count-up test which you see on the screen. The BIOS will generally display a text error message on the screen if it encounters an error at this point; these error messages and their explanations can be found in this part of the Troubleshooting Expert.
- The BIOS performs a "system inventory" of sorts, doing more tests to determine what sort of hardware is in the system. Modern BIOSes have many automatic settings and will determine memory timing (for example) based on what kind of memory it finds. Many BIOSes can also dynamically set hard drive parameters and access modes, and will determine these at roughly this time. Some will display a message on the screen for each drive they detect and configure this way. The BIOS will also now search for and label logical devices (COM and LPT ports).
- If the BIOS support the Plug and Play standard, it will detect and configure Plug and Play devices at this time and display a message on the screen for each one it finds. See here for more details on how PnP detects devices and assigns resources.
- The BIOS will display a summary screen about your system's configuration. Checking this page of data can be helpful in diagnosing setup problems, although it can be hard to see because sometimes it flashes on the screen very quickly before scrolling off the top.
- The BIOS begins the search for a drive to boot from. Most modern BIOSes contain a setting that controls if the system should first try to boot from the floppy disk (A:) or first try the hard disk (C:). Some BIOSes will even let you boot from your CD-ROM drive or other devices, depending on the boot sequence BIOS setting.
- Having identified its target boot drive, the BIOS looks for boot information to start the operating system boot process. If it is searching a hard disk, it looks for a master boot record at cylinder 0, head 0, sector 1 (the first sector on the disk); if it is searching a floppy disk, it looks at the same address on the floppy disk for a volume boot sector.
- If it finds what it is looking for, the BIOS starts the process of booting the operating system, using the information in the boot sector. At this point, the code in the boot sector takes over from the BIOS. The DOS boot process is described in detail here. If the first device that the system tries (floppy, hard disk, etc.) is not found, the BIOS will then try the next device in the boot sequence, and continue until it finds a bootable device.
- If no boot device at all can be found, the system will normally display an error message and then freeze up the system. What the error message is depends entirely on the BIOS, and can be anything from the rather clear "No boot device available" to the very cryptic "NO ROM BASIC - SYSTEM HALTED". This will also happen if you have a bootable hard disk partition but forget to set it active.
This process is called a "cold boot" (since the machine was off, or cold, when it started). A "warm boot" is the same thing except it occurs when the machine is rebooted using {Ctrl}+{Alt}+{Delete} or similar. In this case the POST is skipped and the boot process continues roughly at step 8 above.
23) MBR (master boot record)?
Ans:- The Master Boot Record (MBR) is the information in the first sector of any hard disk or diskette that identifies how and where an operating system is located so that it can be boot (loaded) into the computer's main storage or random access memory. The Master Boot Record is also sometimes called the "partition sector" or the "master partition table" because it includes a table that locates each partition that the hard disk has been formatted into. In addition to this table, the MBR also includes a program that reads the boot sector record of the partition containing the operating system to be booted into RAM. In turn, that record contains a program that loads the rest of the operating system into RAM.
24) Other general OS based questions as what options u have in manage (right click my comp à manage), which logs u have in event viewer, etc..?
Ans: Once you reach there you will find System tools (here we have Event viewer, shared folders, local users & groups, Performance logs & alerts, device manager), Storage (here we have a option for disk management which tells you the file system for each drive), Services & applications.
Event viewer has system, application & security logs. Any errors or success are logged in respective logs. Are helpful in troubleshooting. For e.g. if a print job fails you would have event ID 9 in system log indicating print job failure.